This is a nasty one and more advanced than it appears. Read the "What It Does" section for more detail on that. The e-mail comes pretending to be a WeTransfer link. This is a legitimate file transfer service that's widely used for sending files too big for e-mail. If you're only skimming the e-mail you might overlook that it's coming from WeTransfir instead of WeTransfer. The files you supposedly were sent are vague enough that they'll catch the eye of most expecting something from a customer. Odds are good that you're always waiting for something from someone. These scams, like marketing e-mails and cold calls, are a probability game. They send out a few million e-mails (through their own server or compromised accounts) and see how many people they can get.
An interesting note on this one is the attacker actually owns WeTransfir.com. They're not just spoofing it as usual. This makes it more likely for the e-mail to get through your mail filters if you have any.
The Scam E-Mail
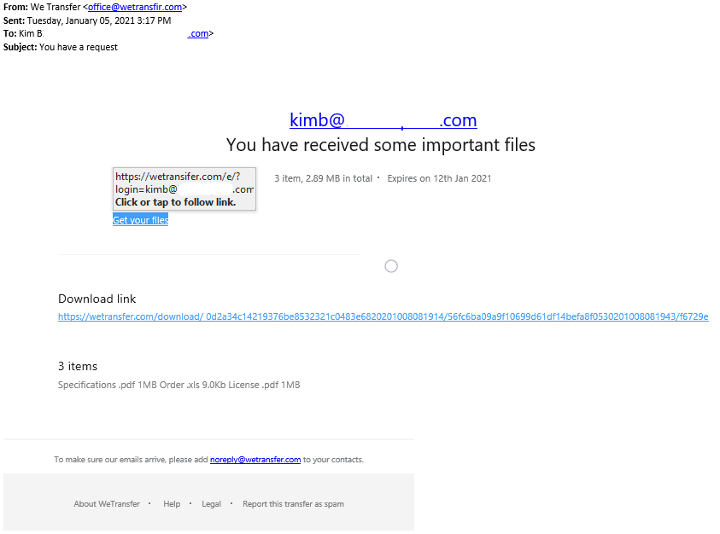
Identifying Traits
Incorrect domain. Rather than WeTransfer it comes from WeTransfir. This is uncommon as large companies usually buy all the domains that look anything like their down to prevent something like this.
Lacks any branding. Vendors are picky about their brand and their company name. This one has none except the little bit at the bottom. It actually looks more legitimate on a phone screen.
Link goes to the wrong website. If you mouseover (without clicking) the link in the e-mail you'll see it goes to WeTransfir instead of WeTransfer. It's a good idea to make a habit of checking this. This is probably the most common tactic scammers use and the one we see overlooked.
What It Does
We had a lot of fun spending a couple hours taking this one apart and it's a nasty piece of work. The first part of the normal credential harvesting we see with these scam e-mails. If you click the link (don't do it!) you're sent to a website hosted on the fake WeTransfir domain asking for your credentials. The fake log in page actually looks very close to the legitimate site. We suspect they just copied the HTML.
While the credential harvesting isn't very nice, the next steps this scam takes are impressive. When you enter your username and password the scam site logs your credentials and attempts to use them on Microsoft's Live authentication page. Too many people use the same username and password on multiple services so the attackers are checking if your credentials work on other sites that have more sensitive and interesting data. This is called "credential stuffing". Once they have your username and password it'll be used on every site they can think of to see what gets through. The site also logs various pieces of information about your computer, who you're logged in as, your IP data, and some code to check for a bot net. The last part caught our attention. We weren't able to dig deep enough into the site to find where it is, but somewhere on the site is likely a bot net downloader/installer it'll try to get you to run. The site says you have files to download so it make sense something in these fake files will be an installer. Bot nets are where some code infects your computer (and a few million other computers) and the attacker can run commands on your computer. Stuff like ransomware, attacking other computers, installing trojans, monitoring keystrokes for credentials, etc. Basically, things you really don't want. In summary, not only does this site take your credentials, it tries to access your personal files on Microsoft servers, and install bot net malware.
We're not 100% certain but this strongly appears to originate in Russia. This is an unfortunately common source of technological shenanigans due to weak international laws. We suspect this due to:
Russian language code snippets.
AK47Loader handles used in the code.
Parts of the code intentionally don't trigger if the viewer is in Russia.
The domain (WeTransfir) is registered in Russia.